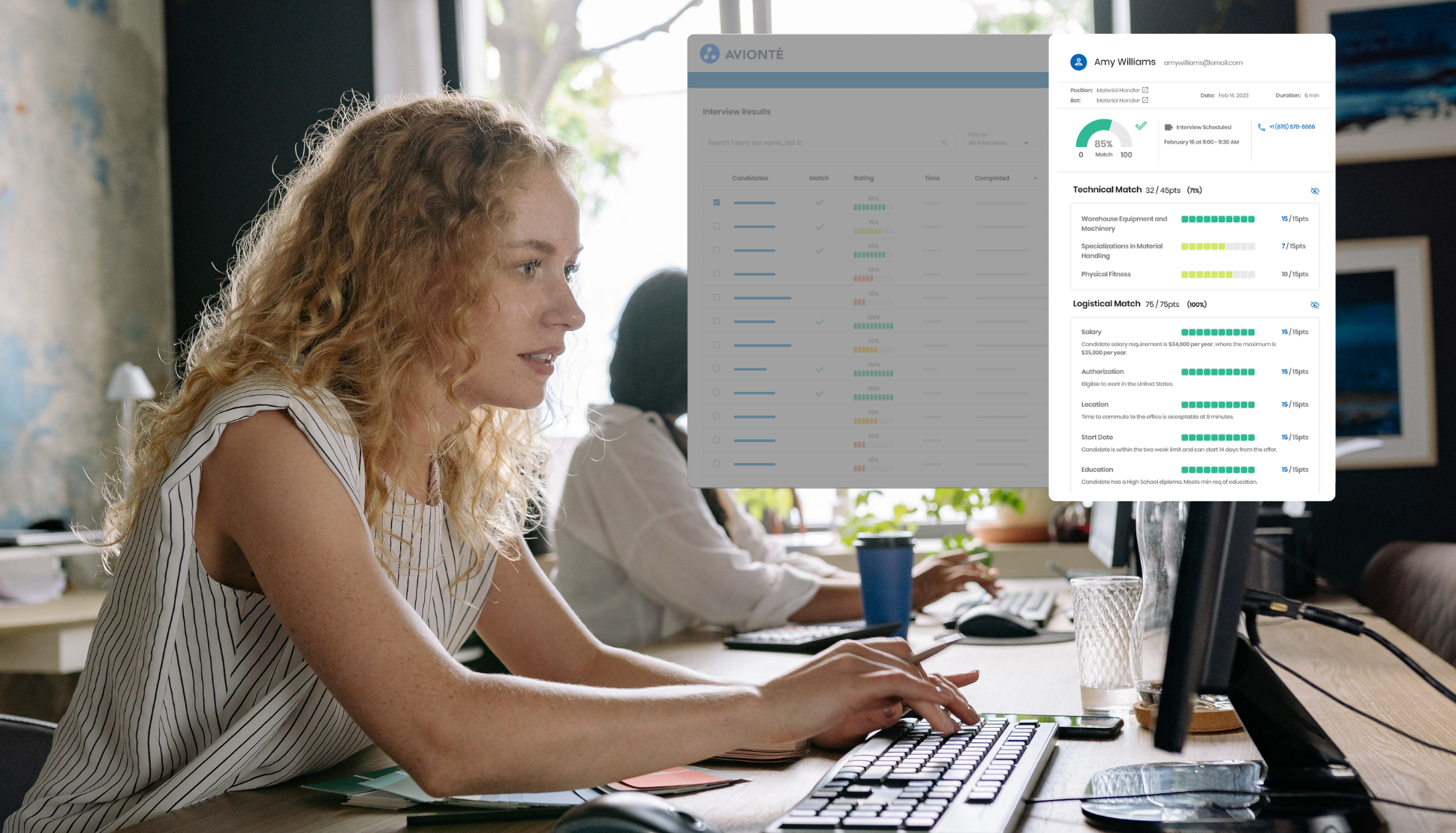
AI Recruiting Workflow for Staffing Agencies: From Job Description to Placement
A workflow for staffing agencies that speeds job posting, screening, and interviews to reduce time to fill and increase placements.
Staffing agencies are prime targets for cybercriminals, and it’s easy to understand why. You’re holding a treasure trove of sensitive data: Social Security numbers, banking details, employment histories, and personal information for thousands of candidates and clients.
The stakes have never been higher. Data breaches in the staffing industry aren’t just inconvenient; they’re existential threats. Agencies that ignored security have paid the price: massive fines, lost trust, and even business-ending consequences. So, how can you safeguard your agency and stay one step ahead in an increasingly dangerous digital landscape?
The good news is that you don’t need to become a cybersecurity expert overnight. By focusing on the three essential steps described below, you can dramatically reduce your risk and build a resilient security posture that protects your business, your clients, and the candidates who trust you with their most sensitive information.

Here’s the uncomfortable truth: even the best security system can be undone by one person clicking the wrong link.
Cybercriminals know this. That’s why phishing and social engineering are their go-to tactics. They’re not trying to hack your firewalls — they’re trying to hack your people.
For staffing agencies, that risk is amplified. Recruiters interact with hundreds of new contacts every week — opening attachments, clicking links, and replying to strangers as part of the job. It’s a perfect environment for attackers to slip in malicious content disguised as legitimate communication.
Building a security-aware culture isn’t optional. It’s essential. The question is how you do it – and it starts with these steps.
Ditch the once-a-year compliance video everyone ignores. Deliver ongoing, practical training that uses real-world examples from the staffing industry. Show actual phishing emails your team might encounter. Make it personal, not theoretical.
Run realistic phishing tests to build instincts. When someone clicks, make it a learning moment, not a reprimand. The goal is to train reflexes and create a culture where people report suspicious messages without fear.
Make it effortless to report threats. Set up a dedicated email or “report phishing” button. Recognize and celebrate employees who speak up, even if it’s a false alarm. In security, overreporting is a strength.
Security culture starts at the top. When executives take training seriously and follow the same protocols, it signals that everyone is accountable.
Your people shouldn’t be your weakest link – they should be your first line of defense. Equip them with the knowledge and confidence to stop attacks before they start. Invest in your team’s awareness with the same urgency you invest in your technology.
If you take away just one thing from this article, let it be this: enable multi-factor authentication on every system, for every user, with no exceptions.
Passwords alone are no longer enough. Even strong, complex passwords can be compromised through phishing attacks, data breaches, or sophisticated hacking techniques. Multi-factor authentication adds a critical second layer of protection by requiring users to verify their identity with something they have (such as a phone or security key) in addition to something they know (their password).
Think of MFA as a deadbolt on top of your regular door lock. Even if someone steals your key (password), they still can’t get in without the second factor.
Here’s why this matters specifically for staffing agencies: your team members are accessing sensitive candidate and client data from various locations and devices. Without MFA, a single compromised password could give cybercriminals unfettered access to your entire database. With MFA enabled, that same compromised password becomes virtually useless.
Your applicant tracking system (ATS), email, financial platforms, and any systems containing PII (personally identifiable information)
Use tools like Google Authenticator or Microsoft Authenticator rather than SMS when possible, as it’s more secure
Executives or “power users” are often the biggest targets
Entering a six-digit code is a minor inconvenience and a small price to pay to avoid the nightmare of explaining a data breach to your clients, making MFA one of your most critical lines of defense.

Let’s tackle a critical question every staffing agency faces: Should your systems be self-hosted or should you, instead, go with a cloud-based vendor with enterprise-level security?
For most agencies, the right answer is simple: Partner with a reputable vendor that lives and breathes security.
Enterprise-grade protection isn’t something you can bolt on. It demands constant investment in infrastructure, expertise, and vigilance: 24/7 security operations centers, penetration testing, compliance audits, dedicated teams, advanced threat detection, and continuous updates to close new vulnerabilities.
Unless you’re running a massive staffing operation with a full-scale IT security division, you can’t match that level of defense, and frankly, you shouldn’t try. Even strong internal IT teams are focused on uptime, user support, and daily operations, not monitoring the dark web or countering zero-day exploits.
Cybersecurity is a specialization, not a side task. Having experts handle it ensures security and allows your team to focus on, instead, what drives your business forward.
Self-hosted or homegrown systems can look attractive on paper. You control everything, customize freely, and avoid subscription fees. But that control comes at a steep – and often hidden – cost. Here’s why:
Every system needs constant maintenance. Miss a single critical patch, and you’ve left an open door for attackers. Enterprise vendors have full-time teams dedicated to staying ahead of known vulnerability — something no internal team can replicate at scale.
Maintaining SOC 2, ISO, and other compliance frameworks isn’t a checkbox exercise — it’s a continuous, expensive process. Vendors distribute those costs across hundreds of clients, giving you enterprise-grade compliance without the overhead.
If your servers fail or ransomware locks you out, what’s your backup plan? Enterprise vendors invest in redundant systems, frequent backups, and tested recovery protocols to keep your business running when disaster strikes.
Cyber threats evolve faster than most IT teams can track. The right vendors employ dedicated security specialists whose sole focus is staying ahead of emerging risks with an expertise that’s nearly impossible to build internally.
As your agency expands, so do the risks. Security complexity increases with every new client, user, and integration. Partnering with the right vendors means their infrastructure scales automatically, giving you enterprise-level protection without the burden of building or maintaining it yourself.
At Avionté, we’ve built enterprise-grade security into the foundation of our platform, so you can focus on growing your business instead of worrying about cyber threats. Our SOC 2 Type 2 certification represents ongoing, rigorous third-party audits of our security controls—proof that we take protection seriously.
We handle security updates, patches, and infrastructure management without the vulnerabilities of self-hosted systems.
Extensive security protocols, vault storage to prevent ransomware attacks, and encryption both at rest and in transit protect your sensitive data.
Serving over 1,000 staffing firms and processing $15+ billion in payroll annually since 2005, we’ve invested in security infrastructure that individual agencies can’t build alone.
Our single, secure system of record covers everything from CRM and ATS to payroll and billing, eliminating vulnerabilities introduced by data moving between disconnected systems.
Security professionals whose sole job is staying ahead of emerging threats, so you benefit from enterprise-level expertise without hiring your own security team.
We’re transparent about our security practices and committed to helping you meet your compliance obligations.
In today’s threat landscape, staffing agencies need a technology partner that delivers both powerful functionality and uncompromising security. Avionté provides both, allowing you to grow your business with confidence.
Protecting your staffing agency from cyber threats isn’t a project you finish – it’s a discipline you maintain. The threat landscape shifts daily, and your defenses must evolve with it.
Start by shoring up your foundation: enforce MFA everywhere, train your team to recognize and resist attacks, and align with partners who deliver enterprise-grade security you can’t replicate in-house. These steps won’t make you bulletproof, but they will make you resilient — and resilience is what keeps your business standing when others fall.
The cost of delay is steep. Every day without these protections is an open invitation to risk. Your clients trust you with their data. Your candidates trust you with their livelihoods. That trust is your brand. Protect it like your business depends on it, because it does.
But having enterprise-grade protection isn’t just a must-have. It’s also a competitive advantage. Think about it: if you can demonstrate to a client or candidate that their data is fully secure, you’re not just mitigating risk; you’re strengthening trust, reinforcing credibility, and turning security into a powerful sales asset.
While other agencies are taking chances and having uncomfortable conversations after a breach, you’re positioned to win business by proving your systems – and your commitments — are reliable and secure.
So, don’t wait for a breach to make security a priority. Act now – before it’s too late.
Ready to learn more about how Avionté can help protect your staffing agency? Contact us and let’s talk about building a more secure future for your business – together. Schedule a free consultation call today.